🎙️ CyberHub Podcast is Back — And So Are the Breaches
Good Morning Security Gang,
After a brief Passover hiatus, host James Azar returned live to the CyberHub Podcast studio with a packed episode spanning supply chain breaches, nation-state attacks, critical vulnerabilities, AI misuse, and government warnings.
With fresh espresso in hand and high energy, the episode kicked off with a quick nod to the success of last week’s deep-dive episodes before diving into this week’s most pressing cybersecurity headlines.
🛒 Ahold Delhaize USA Confirms Major Ransomware Data Breach
Supermarket conglomerate Ahold Delhaize USA, which owns Stop & Shop, Hannaford, Food Lion, and Giant Food, confirmed that threat actors stole data during a cyberattack last fall. The INC Ransomware gang has taken credit, claiming to have exfiltrated 6 terabytes of data. Although operations were temporarily impacted, the company stated its cyber defense capabilities helped contain broader damage. With 2,000+ store locations and $24B in net sales, the breach could affect food access in underserved areas.
🚘 Hertz Breach Tied to Clio Software Supply Chain Vulnerability
Hertz disclosed a breach tied to a supply chain attack on the Clio file transfer platform, revealing attackers accessed sensitive data between October and December 2024. Discovered in February and confirmed in April, the breach did not impact Hertz’s internal network directly. However, it raises questions about whether third-party attacks that don’t result in material business impact should still be reported under SEC guidelines.
🐌 China’s IronHusky Targets Russia and Mongolia with RAT Malware
Kaspersky uncovered a new campaign from the Chinese-speaking IronHusky group using an upgraded Mystery Snail RAT, camouflaged in a malicious MMC script. These attacks are notably targeting Russian and Mongolian government organizations. The malware allows file transfer, command shell access, and persistent backdoor implantation—an extension of RAT tactics observed as early as 2021.
🍎 Apple Issues Emergency Patch for Two Zero-Day Exploits
Apple released out-of-band patches for CVE-2025-31200 and CVE-2025-31201, both being exploited in targeted spyware campaigns. One targets CoreAudio and allows code execution via media file manipulation; the other bypasses pointer authentication protections. Both impact macOS, iPadOS, and iOS devices and underline the need for immediate updates.
🖱️ North Korea, Iran, and Russia Amplify 'ClickFix' Social Engineering
Nation-state actors have adopted a technique dubbed "ClickFix," where fake errors on spoofed websites lead to malware execution via PowerShell. Actors from North Korea (Comiskey), Iran (MuddyWater), and Russia (APT28/UNK Remote Rope) are using this technique for espionage. The infection chain uses deceptive PDFs and fake pop-ups to deploy QuasarRAT and other malware.
💳 NFC Payment Card Scam Targets Android Users with Malware
A sophisticated fraud campaign dubbed "SuperCard X" is exploiting Android's NFC features. Malware-laced apps mimic legitimate payment tools, tricking users into placing their cards near compromised phones to extract money. Inspired by real-world tactics seen in Italy, this scam shows how criminals can exploit contactless payment tech without needing to unlock the device.
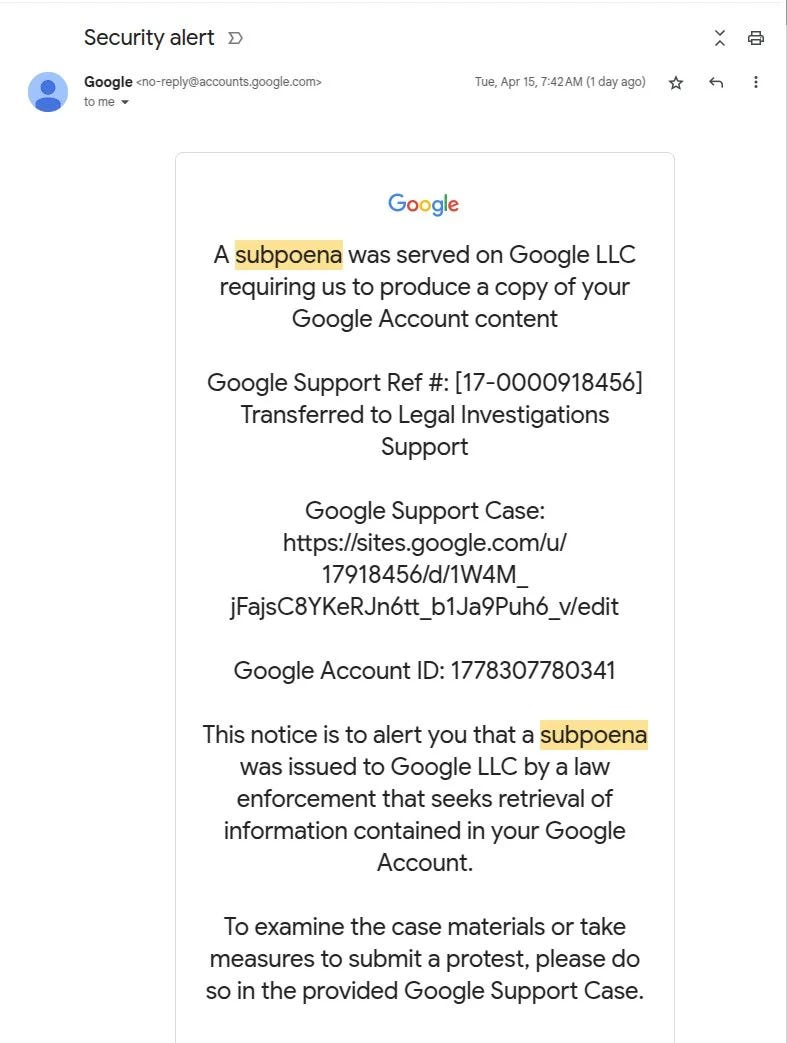
📩 Google’s Own Infrastructure Used in Credential Phishing Scheme
Attackers spoofed Google security alerts and hosted fraudulent pages on Google Sites to collect user credentials. Even experienced developers were nearly duped, underscoring the risks of overreliance on visual legitimacy. The campaign leveraged DKIM-passed emails that appeared authentic, blending phishing with legitimate system notifications.
🤖 Shadow AI Usage Widespread Among Employees
A study by Software AG revealed 50% of employees use AI tools—even if banned by corporate policy. ChatGPT was the most used, and 45% of AI prompts occurred on personal accounts. Shadow AI represents the next iteration of Shadow IT, demanding better corporate controls, flexible AI access, and transparent policies.
🧠 PyTorch Vulnerability Allows Remote Code Execution
A critical flaw (CVE-2025-32434) in PyTorch's torch.load() function undermines model-loading protections and could enable arbitrary code execution even with safe-loading flags enabled. Versions up to 2.5.1 are affected; users should update to 2.6.0 immediately. This poses a major risk for AI model deployment pipelines.
📡 ASUS Routers with AiCloud Feature Vulnerable to Remote Exploits
A high-severity flaw (CVE-2025-24902) affecting ASUS routers with AiCloud capabilities enables remote code execution without authentication. The flaw impacts models across multiple firmware versions, making it critical for users to update. AiCloud turns routers into private cloud servers, amplifying the potential attack surface.
🛍️ Paradise Shops Settles $6.9M Class Action over 2020 Breach
Airport retailer Paradise Shops reached a preliminary $6.9 million settlement with employees affected by a 2020 ransomware attack that exposed Social Security numbers and other PII. The REvil gang reportedly perpetrated the attack. The lawsuit illustrates the long legal tail and financial cost of ransomware incidents.
🧬 U.S. House Report Flags DeepSeek AI as Security Threat
The House Select Committee on the CCP issued a scathing report on China’s DeepSeek AI, warning it poses major risks to national security and personal data privacy. The tool is suspected to feed American data into China’s surveillance ecosystem. The committee recommends tightening export controls and preparing for scenarios where Chinese AI dominance accelerates.
✅ Action List for Practitioners
Update Devices: Apply Apple’s emergency patches (CVE-2025-31200 & 31201) immediately on all iOS/macOS devices.
Patch PyTorch: Upgrade to version 2.6.0+ to mitigate remote code execution risks.
Harden NFC Controls: Financial institutions should reassess and tighten fraud controls for NFC-based transactions.
Mitigate ClickFix Risks: Implement anti-phishing training and endpoint detection to catch advanced lures using fake pop-ups.
Secure Routers: ASUS router users should upgrade firmware to prevent unauthenticated remote access via AiCloud.
Monitor AI Usage: CISOs should create acceptable use policies for GenAI tools and track AI activity to counter Shadow AI.
Review Supply Chain Contracts: Ensure third-party risk management programs include breach reporting requirements—even for non-material incidents.
Enable Payment Alerts: Encourage users to enable phone alerts for small purchases to catch unauthorized NFC taps.
Track Chinese AI Threats: Federal and enterprise security teams should monitor developments in China’s AI tool ecosystem.
🔚 That’s it for today’s episode. Subscribe, share. Until next time — Stay Cyber Safe.
✅ Story Links:
https://therecord.media/dutch-cyberattack-stolen-hannafords-grocery
https://www.cybersecuritydive.com/news/hertz-data-breach-cleo/745391/
https://therecord.media/new-payment-card-scam-involves-malware-tap
https://www.securityweek.com/the-shadow-ai-surge-study-finds-50-of-workers-use-unapproved-ai-tools/
https://www.securityweek.com/apple-pushes-ios-macos-patches-to-quash-two-zero-days/
https://thecyberexpress.com/pytorch-vulnerability-cve-2025-32434/
https://therecord.media/airport-retailer-agrees-to-settlement-ransomware-data-breach
https://cyberscoop.com/deepseek-house-ccp-committee-report-national-security-data-risks/
🔔 Subscribe now for the latest insights from industry leaders, in-depth analyses, and real-world strategies to secure your digital world. https://www.youtube.com/@TheCyberHubPodcast/?sub_confirmation=1
🚨 Important Links to Follow:
👉Website:
👉Listen here: https://linktr.ee/cyberhubpodcast
✅ Stay Connected With Us.
👉Facebook: https://www.facebook.com/CyberHubpodcast/
👉LinkedIn: https://www.linkedin.com/company/cyberhubpodcast/
👉Twitter (X): https://twitter.com/cyberhubpodcast
👉Instagram: https://www.instagram.com/cyberhubpodcast
🤝 For Business Inquiries: info@cyberhubpodcast.com
=============================
🚀 About The CyberHub Podcast.
The Hub of the Infosec Community.
Our mission is to provide substantive and quality content that’s more than headlines or sales pitches. We want to be a valuable source to assist those cybersecurity practitioners in their mission to keep their organizations secure.
Tune in to our podcast Monday through Thursday at 9AM EST for the latest news.