Regulation, Spend, and the Illusion of Security
Why flat budgets, heavy regulation, and shallow incentives are keeping us one step behind attackers — and how smarter, market-driven standards could change that.
Coffee cup cheers, Security Gang.
Every quarter, another new cybersecurity regulation drops — the SEC wants disclosures, Europe brings DORA and NIS2 online, Asia expands data-sovereignty mandates. The alphabet soup is endless.
And yet, despite all these frameworks, our collective cyber posture hasn’t meaningfully improved.
Budgets are flattening heading into 2026, while breaches remain steady or rising. Attackers move faster. Boards feel over-regulated and under-protected.
So, let’s ask the hard question: Is regulation really making us more secure, or just busier?
🧩 Regulation’s Promise — and Its Reality
Regulation was supposed to raise the floor — to make sure everyone, from banks to hospitals, implemented basic hygiene.
In theory, it does. In practice, it often builds a compliance bureaucracy that’s excellent at writing policies and mediocre at defending systems.
Take the SEC’s new cyber-disclosure rule.
It tells public companies when to disclose an incident and how to describe risk management. That’s transparency — good for investors — but it doesn’t actually require firms to detect, contain, or recover faster. It’s reactive, not preventive.
Contrast that with Europe’s Digital Operational Resilience Act (DORA). DORA demands banks and insurers prove operational continuity, conduct regular red-team exercises, and assess ICT-supplier risk. Those are controls — they force muscle-memory.
Then there’s the Cyber Resilience Act (CRA) — it pushes manufacturers to ship products secure-by-design, patch responsibly, and publish SBOMs. Again, proactive.
Across the world, we see two species of regulation:
Control-based — you must do things (DORA, CRA, China’s CSL).
Disclosure-based — you must report things (SEC, CIRCIA, GDPR).
Both have value, but only the former builds actual resilience.
⚖️ What Lawmakers Get Right — and Where They Miss
Here’s the refreshing part: cybersecurity has become one of the few bipartisan issues left.
Across Capitol Hill and Brussels alike, lawmakers agree that digital risk is national-security risk.
“This bipartisan bill renews a proven framework that has helped defend critical networks at our hospitals, financial systems, and energy grids from cyber-attacks.”
— Sen. Gary Peters (D-MI), co-sponsoring with Sen. Mike Rounds (R-SD)
“As technology advances, we must do more to protect Americans’ sensitive data.”
— Rep. Jason Crow (D-CO) with Rep. Brian Fitzpatrick (R-PA)
That’s encouraging — policy cooperation, not politics.
But even within this agreement, the nuance matters.
Most regulations focus on visibility and accountability, not defensive capacity. They ask for incident reports, not intrusion resistance. They shape governance, not grit.
The result? Boards become experts at drafting 8-K filings and policy attestations — while attackers exploit unpatched VPNs.
Lawmakers are focused on the what (disclose, report, attest) when practitioners need the how (detect, contain, recover).
💸 The Spending Spiral Meets the Compliance Trap
From 2019 to 2024, global cybersecurity spend grew from $160 billion to $250 billion — yet breach costs hit record highs.
Why? Because much of that money funded compliance reporting, not capability building.
Meanwhile, 2025 budget surveys show flat growth across most industries. Executives cite AI automation and “regulatory saturation” as reasons to hold spending steady.
Translation: “We’ve spent enough to comply — not enough to compete.”
When regulation consumes the conversation, security becomes a checkbox culture. The paradox is brutal — more rules, same risk.
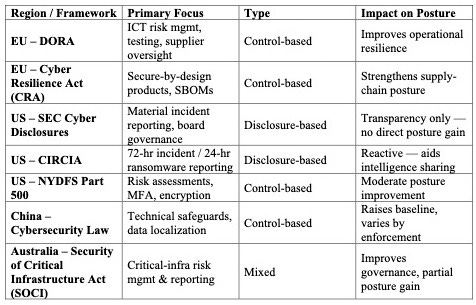
🌍 A Global Look at Regulation — Proactive vs. Reactive
Notice the pattern: the most effective frameworks blend both — they enforce baseline controls and require transparency.
The least effective? Those that stop at “tell us what went wrong.”
🧠 So Why Do We Keep Asking for More Regulation?
Because it’s leverage.
For many CISOs, regulation is the only stick that moves the board.
Say “We need zero-trust funding” — you’re in a debate.
Say “We need zero-trust funding to comply with Article 21 of NIS2” — you’re in motion.
Regulation levels the playing field, but it doesn’t make anyone exceptional.
It provides justification, not transformation.
💬 The Real Question: Do We Need More Regulation — or Better Ones?
Here’s my take: we don’t need more rules. We need smarter ones.
Rules that measure outcomes, not paperwork.
Regulations that drive capability, not compliance.
And, more importantly, we need the free market to reinforce cybersecurity through commerce, not just law.
Think about it — the CMMC model (Cybersecurity Maturity Model Certification) built for DoD suppliers could scale beyond defense.
If large enterprises required vendors to demonstrate maturity tiering based on the data they handle, it would cascade secure behavior down the supply chain.
No Congressional fight, no new law — just market economics rewarding those who secure their operations.
That’s how aviation safety matured. That’s how payment security evolved. And that’s how cybersecurity will scale.
🚀 From Compliance to Competence
CISOs shouldn’t measure success by how many regulations they comply with, but by how quickly they can detect, isolate, and recover.
Boards shouldn’t ask “Are we compliant?” — they should ask “Are we resilient?”
Governments should set minimum floors — but let industry innovation raise the ceiling.
The more energy we pour into smart frameworks (like DORA and CMMC-style assurance models), the less we’ll need to legislate every incident.
☕ James Azar’s CISO Take
After twenty years in this field, my conclusion is simple:
Regulation is the ignition, not the engine.
It sparks awareness, but real propulsion comes from market incentives, business alignment, and operational excellence.
If 2026 is going to be the year of flattened budgets, let it also be the year we flatten bureaucracy.
Let’s replace compliance-driven security with commerce-driven accountability.
We don’t need more regulation — we need poignant, purposeful frameworks that reward maturity, measure outcomes, and empower CISOs to lead with clarity.
Because attackers don’t care how compliant you are.
They care how prepared you are.
Coffee cup cheers,