Good Morning from Israel. Today’s show breakdown is below.
From renewed FCC scrutiny over banned Chinese telecoms to advanced infiltration campaigns by WeaverAnt, the session demonstrates how attackers continually adapt their methods—whether by leveraging compromised routers, concealing malicious web shells, or targeting critical infrastructure. The show also covers significant events like 23andMe’s bankruptcy filing, Ukraine’s resilient railway operations, and a new Van Helsing ransomware-as-a-service threat. Each story underscores the importance of robust cybersecurity controls, coordinated law enforcement efforts, and proactive vulnerability management.
FCC Investigation into Chinese Telecom Providers
The U.S. Federal Communications Commission (FCC) is launching a broad inquiry into whether companies such as Huawei, ZTE, Hikvision, and Dahua, previously deemed national security risks, still operate on American soil. These entities have been barred and removed from federal funding sources. The FCC aims to identify any loopholes or indirect channels these telecom providers might be using to remain active, demonstrating a heightened focus on safeguarding critical telecom infrastructure.
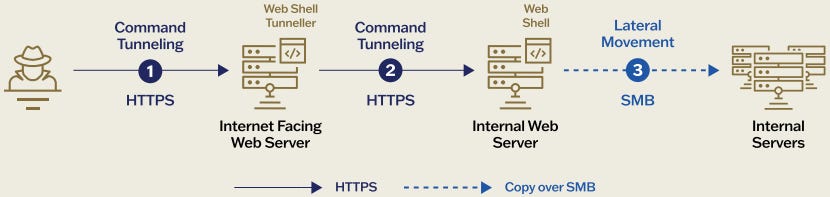
WeaverAnt Exploits Zyxel CPE Routers
An advanced China-linked threat actor dubbed WeaverAnt has infiltrated Asian telecom networks by compromising Zyxel CPE routers. The group uses multiple variants of the China Chopper backdoor and a custom “InMemory” web shell, allowing stealthy just-in-time code execution in the host’s memory. By injecting malicious code into highly trusted processes, WeaverAnt evades standard detection methods and establishes a robust, persistent foothold.
23andMe Files for Bankruptcy
Genetic testing pioneer 23andMe announced it will pursue Chapter 11 bankruptcy following mounting financial difficulties and a damaging cyberattack. The breach eroded consumer trust, particularly as the company’s entire business model hinges on privacy and data security. Authorities in California and the UK advised customers to delete their data and request the destruction of any stored DNA samples, highlighting how loss of trust can hasten a company’s downfall.
Ukraine’s National Railway Operator Hit by Cyberattack
Ukraine’s rail system experienced a major online service disruption, forcing ticket purchases to revert to manual, paper-based methods. Although operational delays ensued, core train services continued without interruption. The incident illustrates effective continuity measures under crisis conditions—an increasingly vital focus in regions prone to large-scale cyberattacks.
Starlink Transmitters Confiscated in Thailand
Thai authorities intercepted 38 Starlink satellite Internet kits destined for scam call centers across the border in Myanmar. Human traffickers and cybercriminal gangs regularly rely on reliable, high-speed connectivity to maintain fraudulent operations. By seizing these transmitters, law enforcement hampers the criminals’ ability to victimize individuals worldwide and underscores the close ties between physical supply chains and cybercrime.
Critical Kubernetes Ingress Engine X Controller Flaws
Researchers identified five critical security flaws (dubbed “Ingress Nightmare”) impacting the Ingress NGINX Controller for Kubernetes. Exploiting these vulnerabilities could allow unauthorized remote code execution and unauthorized access to sensitive secrets. While patches have been released, organizations must act quickly to prevent attackers from hijacking entire clusters via malicious configuration injections and advanced infiltration techniques.
The shortcomings are listed below -
CVE-2025-24513 (CVSS score: 4.8) – An improper input validation vulnerability that could result in directory traversal within the container, leading to denial-of-service (DoS) or limited disclosure of secret objects from the cluster when combined with other vulnerabilities
CVE-2025-24514 (CVSS score: 8.8) – The auth-url Ingress annotation can be used to inject configuration into NGINX, resulting in arbitrary code execution in the context of the ingress-nginx controller and disclosure of secrets accessible to the controller
CVE-2025-1097 (CVSS score: 8.8) – The auth-tls-match-cn Ingress annotation can be used to inject configuration into NGINX, resulting in arbitrary code execution in the context of the ingress-nginx controller and disclosure of secrets accessible to the controller
CVE-2025-1098 (CVSS score: 8.8) – The mirror-target and mirror-host Ingress annotations can be used to inject arbitrary configuration into NGINX, resulting in arbitrary code execution in the context of the ingress-nginx controller and disclosure of secrets accessible to the controller
CVE-2025-1974 (CVSS score: 9.8) – An unauthenticated attacker with access to the pod network can achieve arbitrary code execution in the context of the ingress-nginx controller under certain conditions
Emerging Van Helsing Ransomware-as-a-Service
A new ransomware-as-a-service operation named Van Helsing has surfaced, offering affiliates access to cross-platform attacks targeting Windows, Linux, BSD, ARM, and ESXi. By using a ChaCha20-based encryption method and flexible command-line options, the malware authors cater to both experienced and new threat actors. This evolution demonstrates how quickly ransomware groups adapt and expand to exploit multiple environments simultaneously.
NIST’s Growing Vulnerability Backlog
The National Institute of Standards and Technology (NIST) continues to grapple with a surge in vulnerability submissions—outpacing its capacity to catalog new Common Vulnerabilities and Exposures (CVEs). As the number of zero-day threats and discovered flaws climbs, timely access to vulnerability details becomes an ever more critical cornerstone of proactive cybersecurity strategies.
Action List
Audit Telecom Equipment: Verify compliance and remove banned or suspicious devices from networks.
Harden Router Security: Regularly patch and monitor routers for indicators of compromise, especially if using Zyxel CPE hardware.
Review and Revoke Data Access: For 23andMe users or any compromised service, follow official instructions to delete personal data.
Improve Continuity Plans: Incorporate manual fallback processes to maintain operations during cyber incidents.
Secure Supply Chains: Track shipments of key technological components like satellite transmitters to prevent misuse by criminal organizations.
Patch Kubernetes Ingress Controllers: Apply the latest fixes to avert critical remote code execution vulnerabilities.
Monitor Ransomware Trends: Watch for new multi-platform threats and update defenses accordingly.
Stay Current with CVE Reporting: Leverage AI-driven or automated tools to keep pace with the rapid influx of newly discovered flaws.
✅ Story Links:
https://therecord.media/thai-officers-intercept-starlink-transmitters-myanmar-cyber-scam-compounds
https://thehackernews.com/2025/03/critical-ingress-nginx-controller.html
Level Zero Conference Discount Code: L020RESPOND at www.levelzeroconference.com
🔔 Subscribe now for the latest insights from industry leaders, in-depth analyses, and real-world strategies to secure your digital world. https://www.youtube.com/@TheCyberHubPodcast/?sub_confirmation=1
🚨 Important Links to Follow:
👉Website:
👉Listen here: https://linktr.ee/cyberhubpodcast
✅ Stay Connected With Us.
👉Facebook: https://www.facebook.com/CyberHubpodcast/
👉LinkedIn: https://www.linkedin.com/company/cyberhubpodcast/
👉Twitter (X): https://twitter.com/cyberhubpodcast
👉Instagram: https://www.instagram.com/cyberhubpodcast
🤝 For Business Inquiries: info@cyberhubpodcast.com
=============================
🚀 About The CyberHub Podcast.
The Hub of the Infosec Community.
Our mission is to provide substantive and quality content that’s more than headlines or sales pitches. We want to be a valuable source to assist those cybersecurity practitioners in their mission to keep their organizations secure.
Tune in to our podcast Monday through Thursday at 9AM EST for the latest news.