Good morning, Security Gang!
In today’s Cyber Hub Podcast, the host announces a break for Passover and teases four special pre-recorded episodes focused on topics like Agentic AI and online safety.
Meanwhile, the show dives into a whirlwind of cybersecurity events—from the puzzling Oracle breach communication to major automotive vulnerabilities and regulatory upheavals in Washington. Below is your in-depth, story-by-story recap with actionable insights.
Oracle’s Confusing Breach Disclosure
Oracle’s back-and-forth communication over what it calls “obsolete servers” has left customers perplexed. Initially downplaying leaked credentials, Oracle now confirms some servers were compromised. Although they insist no customer environments were infiltrated, many remain skeptical due to the company’s inconsistent narrative. The situation highlights the importance of clear, transparent incident response to maintain customer trust.
Nissan Leaf Vulnerabilities
Security researchers disclosed multiple CVEs affecting the second-generation Nissan Leaf, revealing the ability to exploit its infotainment system and Bluetooth connection. Attackers could track the car’s location, capture audio, and even manipulate physical car functions (like doors and wipers) while in motion.
The discovery underscores growing concerns around the cybersecurity of connected vehicles, emphasizing the need for robust patching and secure development practices in the automotive industry.
NSA Director Dismissal and Interim Leadership
President Trump’s sudden firing of NSA Director Tim Hugh left Army Lieutenant General William Hartman to testify before the Senate Cyber Subcommittee. While details remain sparse, speculation grows that the White House may be planning a broader reorganization—potentially splitting U.S. Cyber Command from NSA or consolidating them into a newly proposed cyber force. The lack of clarity on long-term strategic direction raises eyebrows in Congress and the security community alike.
Ransomware Attack at Sensata Technologies
Global sensor and component manufacturer Sensata Technologies reported a disruptive ransomware incident to the SEC just days after detecting the breach. Though specifics remain under investigation, the attacker encrypted devices and appears to have exfiltrated proprietary data. Sensata’s rapid disclosure—while details are still emerging—aligns with new SEC reporting rules and highlights the continuing wave of ransomware threats across critical industries.
AI-Fueled Spam Campaign: Akira Bot
Researchers identified “Akira Bot,” an AI-powered platform that blitzes website chats, comment sections, and contact forms with deceptive promotional content. By leveraging machine learning and proxy services, Akira Bot bypasses CAPTCHAs and spam filters with near-humanlike precision. This development warns of a future where automated, AI-driven spam campaigns can evade traditional defenses, elevating the need for behavioral-based detection tools.
AWS SSRF Exploit Campaign
A new threat campaign exploits Server-Side Request Forgery (SSRF) flaws in Amazon Web Services EC2 instances, allowing attackers to collect metadata and escalate privileges via compromised IAM credentials. Armed with these privileges, malicious actors can access S3 buckets and potentially disrupt vital services. Old CVEs dating back to 2017 remain highly targeted, stressing the ongoing importance of timely patching and strict identity-access controls.
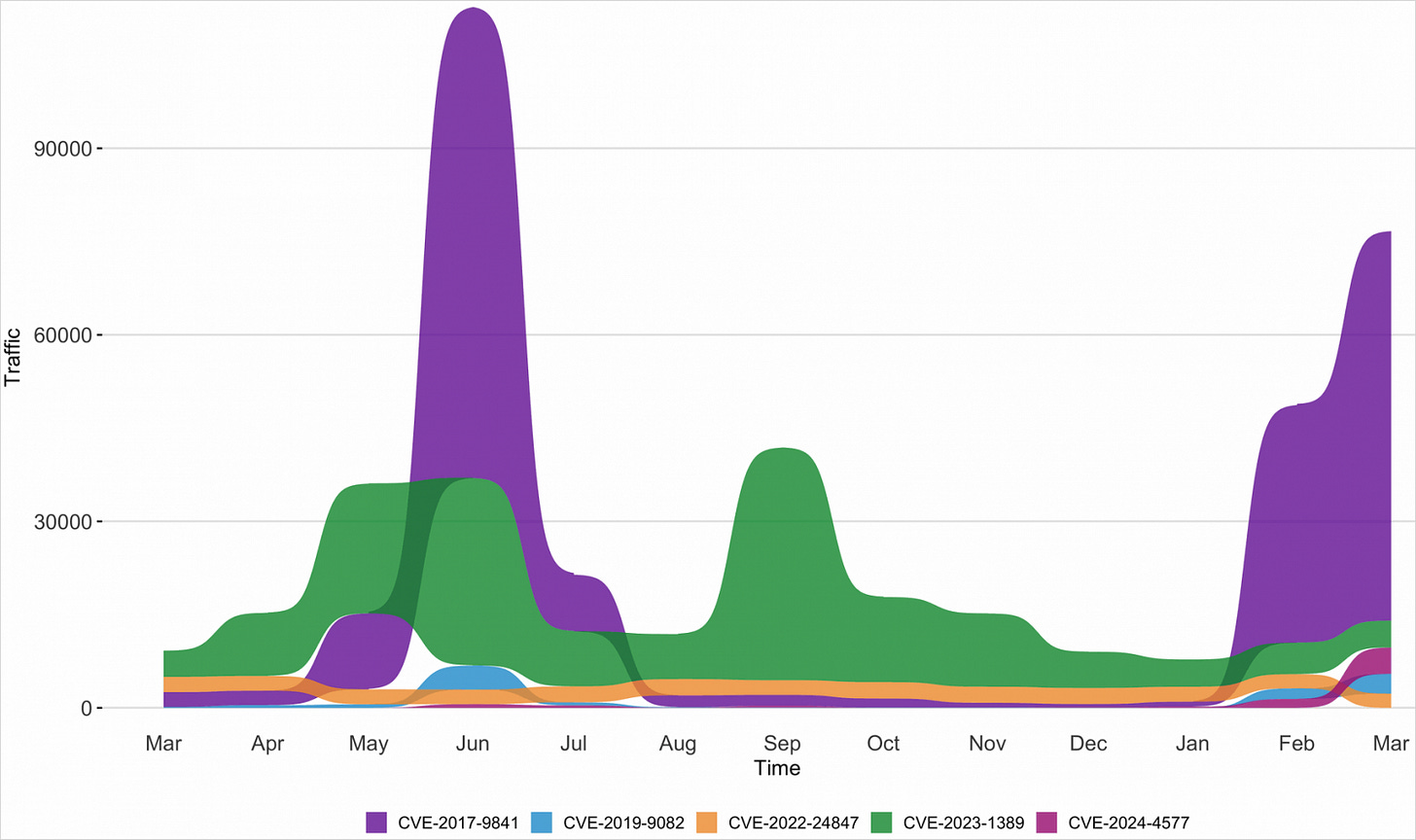
The top four most exploited CVEs by volume were:
CVE-2017-9841 – PHPUnit remote code execution via eval-stdin.php (69,433 attempts)
CVE-2020-8958 – Guangzhou ONU OS command injection RCE (4,773 attempts)
CVE-2023-1389 – TP-Link Archer AX21 command injection RCE (4,698 attempts)
CVE-2019-9082 – ThinkPHP PHP injection RCE (3,534 attempts)
Routers Deemed Riskiest Enterprise Device
A Forescout report designates routers as the “riskiest device” in enterprise environments, citing their high incidence of severe vulnerabilities. Although computers host more bugs overall, routers, firewalls, and Application Delivery Controllers (ADCs) frequently contain the most exploitable weaknesses. As the gateway to corporate networks, they form a prime entry point for attackers, reinforcing the need for rigorous device inventory and proactive patch management.
Google’s Emerging AI IDE Competition
Google is quietly rolling out AI-enhanced integrated development environments (IDEs) in Firebase Studio to compete with services like Cursor AI. While this innovation promises enhanced developer productivity, it also raises new security and compliance challenges. AI-generated code can inadvertently introduce unscanned vulnerabilities—making secure coding practices, code reviews, and scanning tools more critical than ever.
Senator Wyden Blocks CISA Nomination
Senator Ron Wyden is stalling the nomination of Sean Planky as Director of CISA. Wyden demands the release of an unclassified 2022 report detailing security lapses at U.S. telecom companies, accusing CISA of a multi-year cover-up. Critics say holding up critical leadership roles harms the agency’s effectiveness. Supporters of Wyden argue transparency is essential, while opponents see the maneuver as counterproductive to national security.
President Trump Targets Chris Krebs
In a fresh twist, President Trump signed a memorandum revoking Chris Krebs’s security clearance and calling for a probe into potential free-speech violations during Krebs’s tenure at CISA. SentinelOne, Krebs’s current employer, may also be affected as the order extends to associated individuals. This action highlights the ongoing politicization of cybersecurity leadership and complicates public-private partnerships that rely on cleared experts.
Action List
Establish Clear Incident Response Protocols: Oracle’s missteps highlight how consistent, transparent communication protects user trust and minimizes speculation.
Patch Connected Cars Immediately: Automotive manufacturers should expedite patch rollouts for newly discovered vulnerabilities and embed robust security throughout the vehicle’s lifecycle.
Monitor Regulatory Changes: With NSA and CISA leadership in flux, security teams need to stay updated on evolving government cybersecurity directives.
Harden Against Ransomware: Perform frequent backups, maintain robust endpoint protection, and enact segmentations to mitigate damage from ransomware attacks.
Adopt AI Spam Countermeasures: Enhance spam filters and behavioral analysis tools to defend against AI-driven bots like Akira that slip past traditional CAPTCHAs.
Audit Cloud Configurations: SSRF attacks in AWS highlight the importance of AWS metadata hardening, least privilege IAM, and continuous monitoring of cloud instances.
Secure Edge Devices: Prioritize patch management for routers, firewalls, and ADCs, as these remain top targets for cybercriminals.
Implement Secure Coding Practices: With AI-assisted coding on the rise, adopt code scanning tools and thorough reviews to prevent introducing hidden vulnerabilities.
✅ Story Links:
https://www.securityweek.com/nissan-leaf-hacked-for-remote-spying-physical-takeover/
https://therecord.media/hartman-cyber-command-nsa-first-senate-apperance
https://www.securityweek.com/operations-of-sensor-giant-sensata-disrupted-by-ransomware-attack/
https://thehackernews.com/2025/04/akirabot-targets-420000-sites-with.html
https://www.securityweek.com/study-identifies-20-most-vulnerable-connected-devices-of-2025/
https://therecord.media/wyden-blocks-plankey-nomination-cisa
https://therecord.media/trump-memo-chris-krebs-cisa-sentinelone
🔔 Subscribe now for the latest insights from industry leaders, in-depth analyses, and real-world strategies to secure your digital world. https://www.youtube.com/@TheCyberHubPodcast/?sub_confirmation=1
🚨 Important Links to Follow:
👉Website:
👉Listen here: https://linktr.ee/cyberhubpodcast
✅ Stay Connected With Us.
👉Facebook: https://www.facebook.com/CyberHubpodcast/
👉LinkedIn: https://www.linkedin.com/company/cyberhubpodcast/
👉Twitter (X): https://twitter.com/cyberhubpodcast
👉Instagram: https://www.instagram.com/cyberhubpodcast
🤝 For Business Inquiries: info@cyberhubpodcast.com
=============================
🚀 About The CyberHub Podcast.
The Hub of the Infosec Community.
Our mission is to provide substantive and quality content that’s more than headlines or sales pitches. We want to be a valuable source to assist those cybersecurity practitioners in their mission to keep their organizations secure.
Tune in to our podcast Monday through Thursday at 9AM EST for the latest news.