Good morning, security gang! In this episode of the CyberHub Podcast, the host returns from Tel Aviv with stories of vibrant coffee culture and a fresh load of Israeli espresso. Beyond the personal anecdotes, the episode delves into critical cyber events shaping the global security landscape, from Sam's Club possibly facing a high-profile ransomware breach, to Oracle Health grappling with a legacy server compromise, to newly discovered vulnerabilities in solar energy infrastructure.
The podcast concludes with discussion on emerging legislation and free speech concerns in the UK, highlighting the broad spectrum of issues impacting modern cybersecurity.
Sam’s Club (Walmart) Ransomware Allegations
A high-stakes claim has emerged from the CLOP ransomware gang, who added Sam’s Club to their dark web leak site. While Sam’s Club has not officially confirmed the data breach, the situation underscores the difficulties of third- and fourth-party risks. Practitioners everywhere are reminded that when a large supply chain or service provider is compromised, determining which internal systems or partners might be affected can become a lengthy, resource-intensive needle-in-the-haystack process.
Oracle Health Data Breach
Oracle Health—formerly Cerner—alerted its customers that a legacy data migration server was breached in February. Threat actors used compromised customer credentials, raising questions about potential connections to a larger Oracle Cloud SSO compromise. Some UAE government entities (around thirty government agencies) also acknowledged being impacted, indicating that the overall fallout from the Oracle Cloud vulnerabilities could affect millions of records worldwide. The incident highlights how a single breach across shared infrastructure can ripple through public and private sectors on a global scale.
Solar Energy Vulnerabilities
With solar energy’s growing popularity, especially for individual homes, power plants, and off-grid communities, new research warns of ninety vulnerabilities in systems by SunGrow, GrowWatt, and SMA. A key concern is that attackers leveraging these flaws could cause large-scale instability within power grids by compromising numerous inverters. These findings emphasize the heightened necessity for robust patching policies and ongoing vigilance in the renewable energy sector.
Firefox Vulnerability (Similar to Chrome Zero-Day)
Mozilla has released patches for a critical sandbox escape vulnerability (CVE-2023-28557) that closely mirrors a recently addressed Chrome zero-day. Although Kaspersky found the Chrome exploit actively used against Russian organizations, Firefox’s analysis showed it also contained IPC code flaws. The bug affects Firefox on Windows and has been patched in the latest browser releases, underscoring the importance of rapidly updating all browsers—especially in organizational environments.
Splunk Security Updates
Splunk published patches addressing multiple flaws in Splunk Enterprise and its Secure Gateway app, including two high-severity vulnerabilities with potential remote code execution. One particularly severe bug (CVE-2023-20229) arises from a missing authentication check, reminding enterprises to stay vigilant with regular patch cycles. Disabling or removing unused Splunk features is a temporary workaround if full patching is not immediately possible.
Tracked as CVE-2025-20229 (CVSS score of 8.0), the security defect is caused by a missing authorization check, and has been addressed with the release of Splunk Enterprise versions 9.4.0, 9.3.3, 9.2.5, and 9.1.8, and Splunk Cloud Platform versions 9.3.2408.104, 9.2.2406.108, 9.2.2403.114, and 9.1.2312.208. Splunk Enterprise versions 9.4.1, 9.3.3, 9.2.5, and 9.1.8, and in Secure Gateway versions 3.8.38 and 3.7.23.
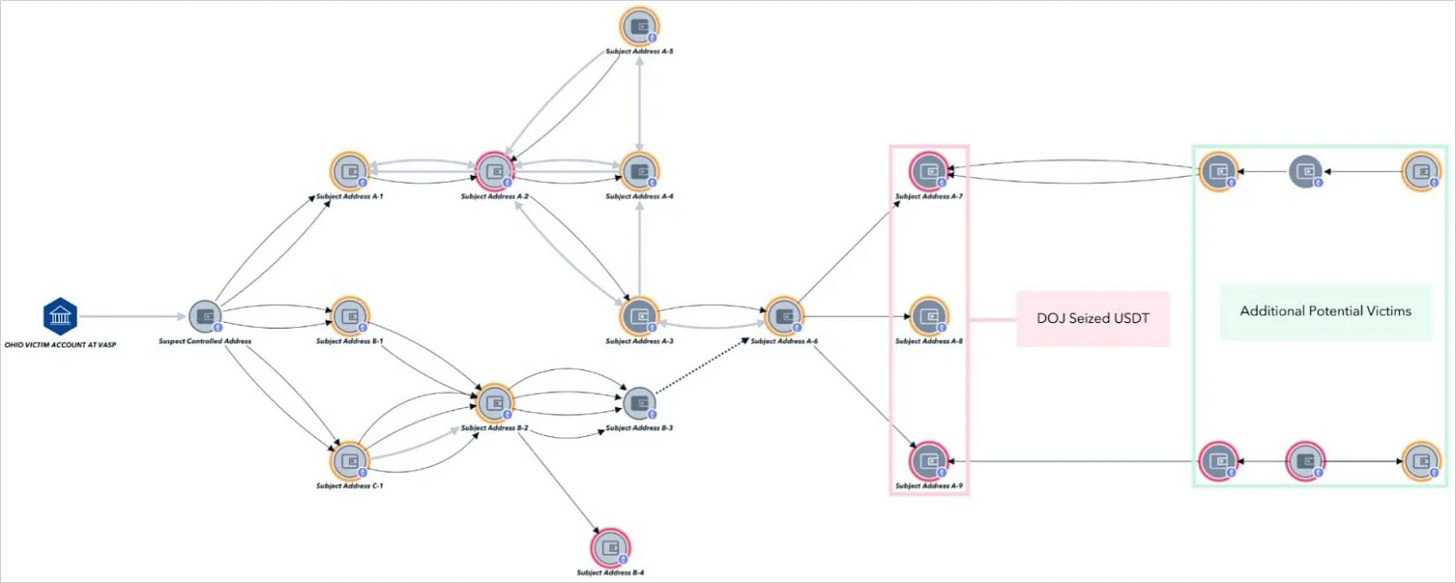
DOJ Seizes $8.2 Million in Romance Scam Proceeds
Romance-baiting scams remain a profitable vector for cybercriminals, often convincing victims to invest in fake platforms. The U.S. Department of Justice, partnering with blockchain analytics investigators, managed to freeze over eight million dollars in Tether (USDT). Working with Tether Limited, they tracked illicit wallets, burned compromised tokens, and reissued them under law enforcement’s control. The success story showcases how collaboration between law enforcement and crypto platforms can hamper criminal operations.
Russian-Speaking Red Curl Threat Actor
Bitdefender researchers discovered that the espionage-focused group Red Curl (also known as Earth Caper or Red Wolf) has adopted a new ransomware strain, QW Crypt. Red Curl conducts highly targeted attacks primarily for corporate espionage, but it has started deploying a specialized ransomware component to shut down virtualized infrastructures. By focusing on hypervisors and carefully selecting which systems to encrypt, the group maximizes disruption while keeping critical access in place to maintain footholds.
UK Free Speech Concerns
The UK’s new Online Safety Act is sparking debates around potential conflicts with free speech and content moderation. Although some officials portray the law as a necessary measure against harmful online activities, critics highlight scenarios where citizens have been approached or even arrested by law enforcement simply for criticizing public figures or institutions online. The host underscores that while regulating illegal or harmful content is important, broad legal measures risk stifling open dialogue and dissent, challenging the very nature of democratic freedoms.
Action Items
Monitor Supply Chain: Immediately audit your third-party and fourth-party vendors for vulnerabilities and intrusion attempts, especially in light of large-scale breaches (e.g., Sam’s Club, Oracle Health).
Strengthen Access Management: Reassess and tighten credential management practices to mitigate risks like the compromised customer credentials seen in Oracle’s breach.
Patch Solar Infrastructure: For organizations using solar systems, promptly apply any new security updates from SunGrow, GrowWatt, and SMA to prevent grid-related exploits.
Update Browsers: Ensure all endpoints are running the latest versions of Firefox, Chrome, and other browsers to safeguard against sandbox escapes and zero-day threats.
Regularly Patch Splunk and Other Core Services: If you rely on Splunk Enterprise or Secure Gateway apps, prioritize these patches; disable features not in active use.
Secure Cryptocurrency Operations: For institutions or individuals dealing in crypto, maintain a robust KYC (Know Your Customer) and AML (Anti-Money Laundering) policy to address romance-baiting scams or similar fraud.
Review Incident Response Plans: Ransomware groups, like Red Curl, increasingly leverage targeted encryption on critical hypervisors. Conduct tabletop exercises and ensure backups are segmented to maintain business continuity.
Advocate for Balanced Legislation: Stay informed on the UK’s Online Safety Act and advocate responsible enforcement to uphold security while preserving free speech principles.
✅ Story Links:
https://thecyberexpress.com/massive-uae-cyberattack-blocked/
https://www.securityweek.com/more-solar-system-vulnerabilities-expose-power-grids-to-hacking/
https://www.securityweek.com/splunk-patches-dozens-of-vulnerabilities/
https://www.securityweek.com/russian-espionage-group-using-ransomware-in-attacks/
https://therecord.media/uk-online-safety-act-us-social-media-jd-vance
🔔 Subscribe now for the latest insights from industry leaders, in-depth analyses, and real-world strategies to secure your digital world. https://www.youtube.com/@TheCyberHubPodcast/?sub_confirmation=1
🚨 Important Links to Follow:
👉Website:
👉Listen here: https://linktr.ee/cyberhubpodcast
✅ Stay Connected With Us.
👉Facebook: https://www.facebook.com/CyberHubpodcast/
👉LinkedIn: https://www.linkedin.com/company/cyberhubpodcast/
👉Twitter (X): https://twitter.com/cyberhubpodcast
👉Instagram: https://www.instagram.com/cyberhubpodcast
🤝 For Business Inquiries: info@cyberhubpodcast.com
=============================
🚀 About The CyberHub Podcast.
The Hub of the Infosec Community.
Our mission is to provide substantive and quality content that’s more than headlines or sales pitches. We want to be a valuable source to assist those cybersecurity practitioners in their mission to keep their organizations secure.
Tune in to our podcast Monday through Thursday at 9AM EST for the latest news.