Welcome to the latest edition of the Cyber Hub Podcast, where we unpack critical cybersecurity developments shaping the industry over the last twenty-four hours.
This episode covers high-profile U.S. indictments against Chinese nationals allegedly tied to cyberattacks on the Treasury, evolving tactics by a notorious Chinese APT, severe VMware zero-day threats, and new concerns around botnets in off-brand Android devices.
Additionally, we explore the impact of incident-reporting requirements on critical infrastructure and highlight an extradition case involving multinational cybercrime. Below is a comprehensive breakdown of each major story, followed by a concise action list to help you address these threats proactively.
U.S. Charges Chinese Nationals in Treasury Cyberattack
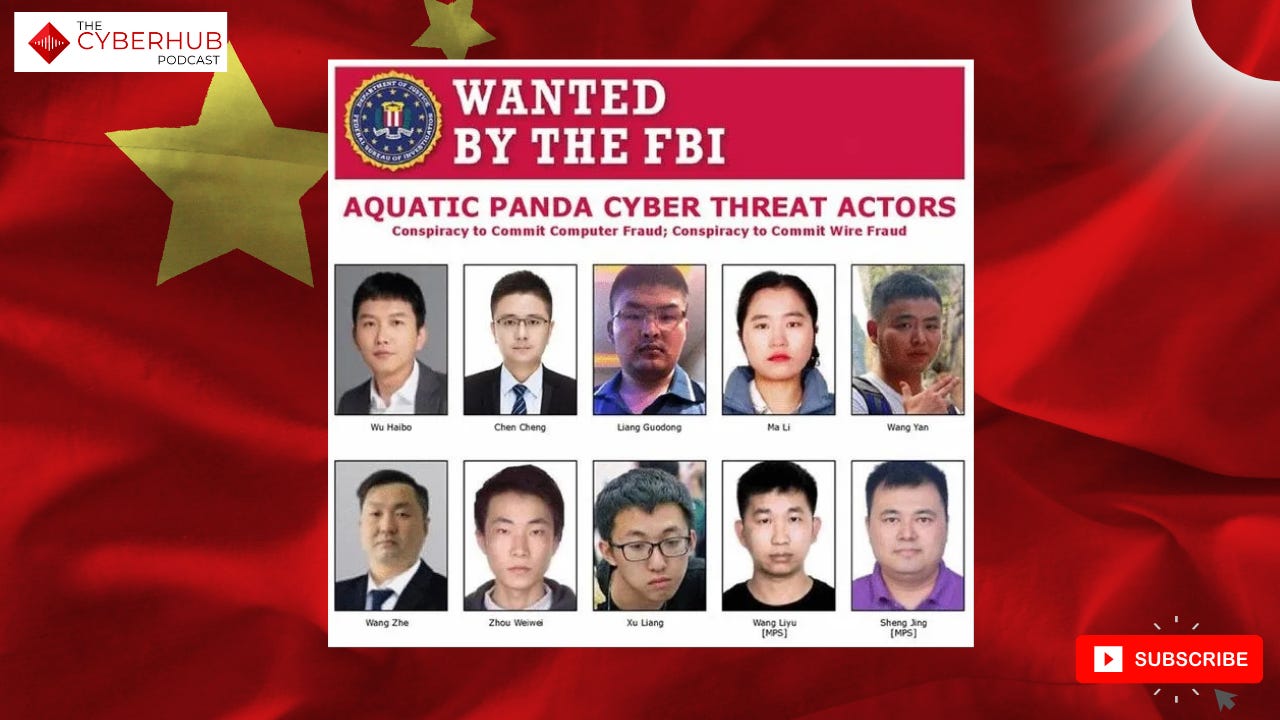
The U.S. Department of Justice unsealed indictments against twelve Chinese nationals for their alleged roles in hacking the Treasury and other significant targets. Two of the accused are Ministry of Public Security (MPS) officers, while several others are tied to a cybersecurity firm known as I soon, which is believed to sell stolen data to multiple branches of the Chinese government. Charged with targeting government agencies, journalists, and religious organizations between 2016 and 2023, these actors used advanced techniques to access email accounts, servers, and proprietary data.
Although extradition is highly unlikely, these indictments severely restrict the suspects’ international movements and expose their operations.
Microsoft Alert on Silk Typhoon’s New Tactics
Microsoft warned that Chinese state-sponsored group Silk Typhoon has adjusted its modus operandi. Beyond exploiting unpatched devices and VPN vulnerabilities, the group increasingly pivots to targeting remote management tools and cloud services, facilitating downstream breaches in multiple sectors—healthcare, government, NGOs, and beyond. Leveraging stolen credentials, they infiltrate victim networks, abuse Microsoft services, and maintain persistence for extended espionage campaigns.
The shift to supply chain compromises underscores the heightened vigilance organizations must maintain around vendors and remote software tools.
VMware ESXi Zero-Day Threats
CISA has added three newly discovered VMware ESXi vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog. More than forty-one thousand ESXi instances remain unpatched worldwide, making them prime targets for ransomware and other cyberattacks. Threat actors exploiting these flaws can gain complete server access, potentially compromising everything from VMs to sensitive configurations.
Experts warn that an “ESXi Cape” scenario—once attackers gain control of ESXi—could facilitate widespread lateral movement across virtualized environments. Organizations are urged to patch immediately given the proven real-world exploits already circulating.
One Million Off-Brand Android Devices Form Botnet
Researchers identified a massive botnet incorporating at least one million Android devices. Many are cheap, off-brand gadgets produced in China—ranging from TV streaming boxes to car infotainment systems—that come preloaded with backdoors. Previously dubbed “Bad Box,” the campaign was disrupted but has since resurfaced.
Concentrated primarily in South America, the botnet highlights the growing risk of cheaply made devices that circumvent quality and security controls, allowing malicious actors to create large-scale armies for DDoS attacks, data exfiltration, or other nefarious activities.
Microsoft Sign Driver Vulnerability Exploited
The CERT Coordination Center (CERT/CC) warns of five vulnerabilities in Paragon Software’s BioNTDrive.sys driver, used within Microsoft-signed components. Ransomware groups have adopted a “Bring Your Own Vulnerable Driver” (BYOVD) technique by introducing signed-yet-flawed drivers to compromise Windows systems.
At least one of these vulnerabilities has already been exploited in the wild, signaling a growing trend where attackers bypass security controls using legitimately signed but maliciously leveraged tools.
Incident Reporting Under Scrutiny by Financial Institutions
A group of financial organizations has sent an open letter urging CISA to revise proposed rules tied to the Cyber Incident Reporting for Critical Infrastructure Act (CIRCA) of 2022. While the law mandates reporting within seventy-two hours of a major cyber incident—and within twenty-four hours for ransomware payments—industry leaders contend that the proposed implementation places heavy operational burdens on victims.
They argue that excessive administrative tasks impede swift response and recovery, advocating instead for a balanced approach that better aligns with real-world incident dynamics.
Nigerian Cybercriminals Extradited to the U.S.
Two Nigerian nationals face charges in the U.S. over their alleged involvement in large-scale tax fraud operations and computer intrusions targeting American tax preparation companies. After deploying phishing campaigns and remote access trojans, the suspects reportedly stole personal data for filing fraudulent returns and laundering funds across multiple countries.
One individual was arrested in the U.K. and extradited to the U.S., highlighting ongoing international law enforcement cooperation in dismantling cybercrime networks.
Action Items
Patch Critical Servers Immediately
Prioritize VMware ESXi updates and investigate any unpatched systems or vulnerable Microsoft drivers.Review Supply Chain Security
Assess remote management tools and third-party partnerships, especially given Silk Typhoon’s tactic shift.Implement Botnet Detection & Network Segmentation
Monitor network traffic for suspicious off-brand devices and isolate IoT/streaming boxes in a separate VLAN.Scrutinize BYOVD Risks
Enhance endpoint detection and response (EDR) rules to flag anomalous driver installations, even if they appear signed.Reinforce Incident Response Plans
Stay informed on evolving federal reporting mandates. Balance compliance requirements with immediate containment measures.Limit Cheap Device Deployments
Encourage procurement teams to vet the security credentials of consumer-grade electronics before deployment or resale.Collaborate with Law Enforcement
In the event of data theft or international fraud, proactive communication can expedite arrests and asset recovery.
Stay Cyber Safe!
✅ Story Links:
https://therecord.media/doj-charges-chinese-nationals-isoon-cyberattacks-treasury
https://www.bankinfosecurity.com/us-prosecutors-indict-isoon-chinese-hacking-contractors-a-27650
https://www.bankinfosecurity.com/malware-infested-android-devices-fuel-global-botnet-fraud-a-27654
https://www.cybersecuritydive.com/news/microsoft-signed-driver-used-in-ransomware-attacks/741372/
https://www.securityweek.com/nigerian-accused-of-hacking-tax-preparation-firms-extradited-to-us/
🔔 Subscribe now for the latest insights from industry leaders, in-depth analyses, and real-world strategies to secure your digital world. https://www.youtube.com/@TheCyberHubPodcast/?sub_confirmation=1
🚨 Important Links to Follow:
👉Website:
👉Listen here: https://linktr.ee/cyberhubpodcast
✅ Stay Connected With Us.
👉Facebook: https://www.facebook.com/CyberHubpodcast/
👉LinkedIn: https://www.linkedin.com/company/cyberhubpodcast/
👉Twitter (X): https://twitter.com/cyberhubpodcast
👉Instagram: https://www.instagram.com/cyberhubpodcast
🤝 For Business Inquiries: info@cyberhubpodcast.com
=============================
🚀 About The CyberHub Podcast.
The Hub of the Infosec Community.
Our mission is to provide substantive and quality content that’s more than headlines or sales pitches. We want to be a valuable source to assist those cybersecurity practitioners in their mission to keep their organizations secure.
Tune in to our podcast Monday through Thursday at 9AM EST for the latest news.