Good morning, security gang! In this episode of the CyberHub Podcast, listeners are welcomed with the host’s lively banter about recovering from St. Patrick’s Day festivities and embracing the need for strong cybersecurity.
The host sets the stage by highlighting a packed show filled with ransomware updates, data breach revelations, and critical vulnerability warnings. The importance of a swift, espresso-like rundown of cybersecurity happenings is emphasized, underscoring that the format is intended to be concise yet thorough.
Western Alliance Bank Data Breach
Western Alliance Bank notified approximately 22,000 individuals that their personally identifiable information (PII) had been stolen from a third-party secure FTP service. An unknown vulnerability dating back to October of the previous year allowed threat actors to access parts of Western Alliance’s systems and steal files containing names, Social Security numbers, dates of birth, driver’s license numbers, passport details, financial account information, and tax identification numbers.
The discovery and subsequent timeline indicate a potential lapse in security oversight. The incident underscores the ongoing challenges financial institutions face when relying on older or insufficiently monitored third-party file-transfer protocols.
Mora Ransomware Exploiting Fortinet Bug
A ransomware group known as Mora (or Mora001) has been exploiting a Fortinet vulnerability that CISA highlighted in January. This group appears to be an offshoot of the LockBit ransomware operation, illustrating the decentralized nature of cybercrime.
Threat actors involved in LockBit simply reassemble under new names whenever core infrastructure is taken down. The U.S. government mandated federal agencies to patch CVE-2022-42475 and CVE-2022-39947 on Fortinet firewalls and VPNs within a strict deadline, given the severity of the vulnerability.
BlackBasta’s Private Chat Leak
Private chat logs from the BlackBasta ransomware gang were leaked, revealing a brute-forcing framework called “Brooted.” This tool specifically targets VPNs, firewalls, and other network-edge devices. Often, success in these attacks stems from weak or reused passwords.
The framework’s methodology includes collecting data on subdomains and IP addresses, then generating credible HTTP/HTTPS requests to mirror legitimate VPN or RDP client traffic. The incident highlights the need for strong password practices, regular credential changes, and continuous monitoring, especially as threat actors adopt increasingly sophisticated techniques.
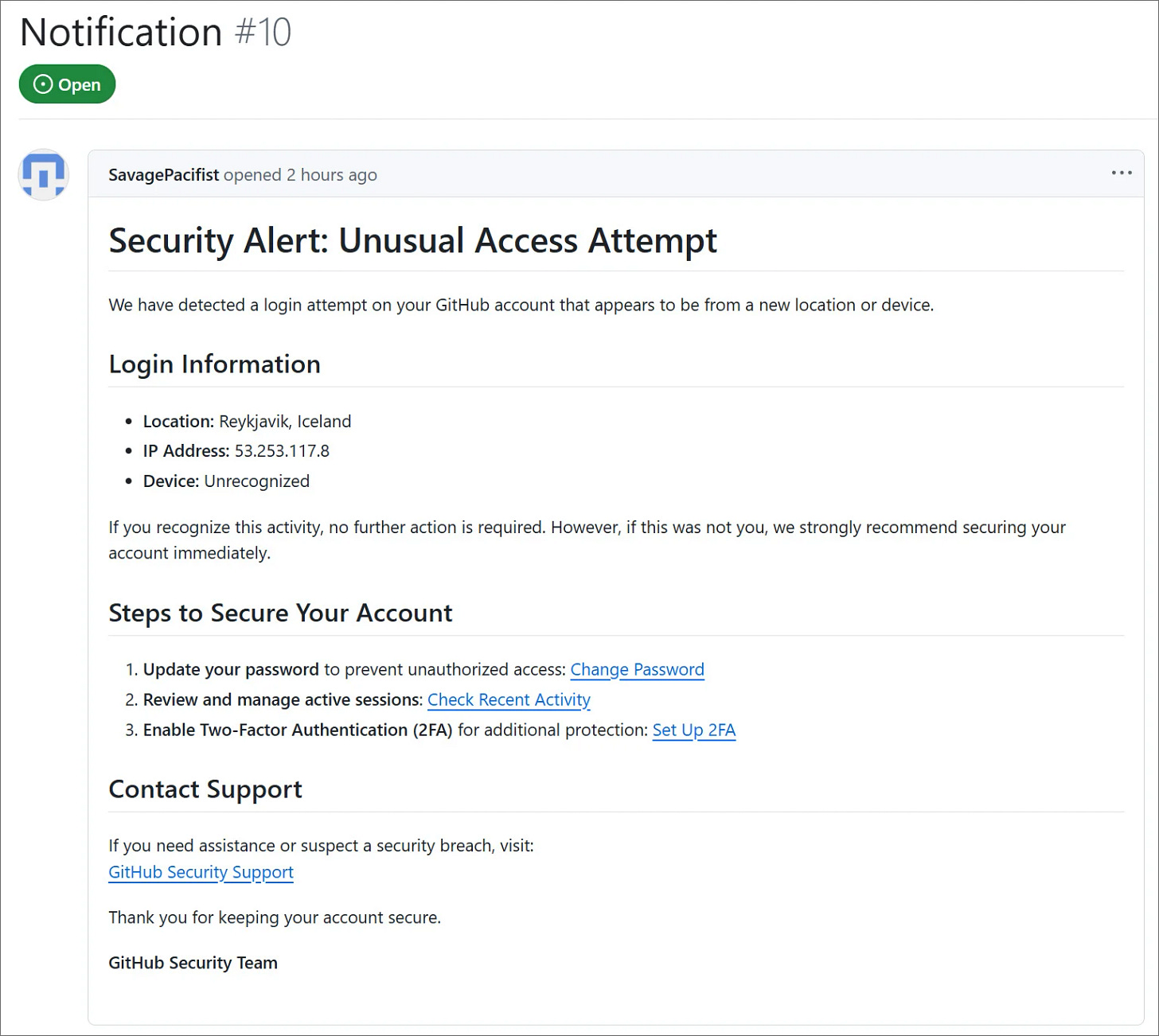
GitHub Phishing Campaign
A widespread phishing campaign hit nearly 12,000 GitHub repositories with fake security alert messages. These alerts lured developers to authorize a malicious OAuth application that requests full control over user accounts and code repositories.
The phony notification mimics legitimate GitHub security alerts, urging developers to reset their passwords and enable MFA. Those who fall for the trick risk complete compromise of their codebase. Developers are strongly advised to enable MFA via an authenticator app rather than SMS to mitigate interception attacks.
Apache Tomcat Vulnerability
An exploit code for a critical remote code execution vulnerability in Apache Tomcat was recently posted on a Chinese forum, allowing attackers to hijack servers using a single PUT request. Tracked as CVE-2023-24813, the vulnerability affects multiple Apache Tomcat versions and can be exploited without any authentication or user interaction. The Apache Tomcat vulnerability, tagged as CVE-2025-24813 and patched last Monday with an important-severity rating, affects Apache Tomcat 11.0.0-M1 to 11.0.2, 10.1.0-M1 to 10.1.34, and 9.0.0.M1 to 9.0.98.
The attack uses base64 encoding to bypass security filters. Once the malicious code is placed in Tomcat’s session storage, a crafted GET request forces deserialization, granting attackers complete control over the compromised system. Immediate patching is strongly recommended.
Telegram CEO Pavel Durov Allowed to Leave France
After months of being detained in France over a criminal investigation related to Telegram’s moderation and cooperation practices, founder Pavel Durov has been granted permission to leave the country.
Durov, who relocated Telegram’s headquarters to Dubai in 2017, expressed gratitude to the French judges and his legal team. This development follows heightened scrutiny by French authorities regarding Telegram’s approach to content moderation and lawful data access.
Former Uber CSO Joe Sullivan Sentencing Upheld
An appellate court has upheld the sentence given to Joe Sullivan, former Chief Security Officer at Uber. Sullivan previously received three years of probation for his role in failing to disclose a data breach to regulators. Prosecutors contested the leniency of the sentence but were ultimately unsuccessful in their appeal. This final ruling brings closure to a prominent case, reinforcing the legal responsibilities of cybersecurity executives when breaches occur.
Infosys McCamish Class Action Settlement
Indian IT giant Infosys announced that its U.S. subsidiary, Infosys McCamish Systems, will pay USD 17.5 million to settle six class action lawsuits tied to a cybersecurity incident that compromised the personal information of over six million people.
The settlement was reached without admitting liability, signaling the complexity of large-scale data breaches and the high costs of subsequent litigation. A considerable portion of the funds typically goes to legal fees, while victims may receive relatively modest sums.
NIST Adds Fifth Post-Quantum Cryptography Algorithm
The National Institute of Standards and Technology (NIST) is expanding its post-quantum cryptography (PQC) portfolio with a fifth algorithm, known as HQC.
This addition complements the existing quantum-resistant algorithms Crystals-Kyber, Crystals-Dilithium, Falcon, and SPHINCS+. Draft standardization for HQC is expected in 2026, with a finalized standard arriving by 2027. This move aligns with preparations for the quantum era, ensuring cryptographic resilience against future quantum attacks.
Action Items
Review Third-Party File Transfers: Minimize or eliminate the storage of PII on FTP servers.
Patch Fortinet Products: Immediately apply patches to critical Fortinet firewall and VPN vulnerabilities.
Implement Strong Access Controls: Use robust password policies and MFA for all network-edge devices.
Educate Developers: Warn GitHub users about phishing scams and require MFA via authenticator apps.
Update Apache Tomcat: Patch Tomcat systems promptly to avoid RCE exploits.
Monitor Legal Obligations: Security leaders should stay informed about regulatory requirements to handle data breaches responsibly.
Plan for Post-Quantum: Begin testing and planning for quantum-safe cryptographic solutions in your organization.
Stay informed, stay alert, and as always—stay cyber safe!
✅ Story Links:
https://www.securityweek.com/western-alliance-bank-discloses-data-breach-linked-to-cleo-hack/
https://therecord.media/mora001-ransomware-gang-exploiting-vulnerability-lockbit
https://therecord.media/telegram-pavel-durov-leaves-france-amid-probe
https://therecord.media/joe-sullivan-former-uber-executive-conviction-upheld
https://www.bankinfosecurity.com/infosys-settles-data-breach-class-action-lawsuits-for-175m-a-27746
https://www.securityweek.com/nist-announces-hqc-as-fifth-standardized-post-quantum-algorithm/
Level Zero Conference Discount Code: L020RESPOND at www.levelzeroconference.com
🔔 Subscribe now for the latest insights from industry leaders, in-depth analyses, and real-world strategies to secure your digital world. https://www.youtube.com/@TheCyberHubPodcast/?sub_confirmation=1
🚨 Important Links to Follow:
👉Website:
👉Listen here: https://linktr.ee/cyberhubpodcast
✅ Stay Connected With Us.
👉Facebook: https://www.facebook.com/CyberHubpodcast/
👉LinkedIn: https://www.linkedin.com/company/cyberhubpodcast/
👉Twitter (X): https://twitter.com/cyberhubpodcast
👉Instagram: https://www.instagram.com/cyberhubpodcast
🤝 For Business Inquiries: info@cyberhubpodcast.com
=============================
🚀 About The CyberHub Podcast.
The Hub of the Infosec Community.
Our mission is to provide substantive and quality content that’s more than headlines or sales pitches. We want to be a valuable source to assist those cybersecurity practitioners in their mission to keep their organizations secure.
Tune in to our podcast Monday through Thursday at 9AM EST for the latest news.